
Raising awareness of cyber threats and defences
Can attacker’s threats beat the defender’s security posture?
Practice cybersecurity decision-making
Three games of increasing complexity
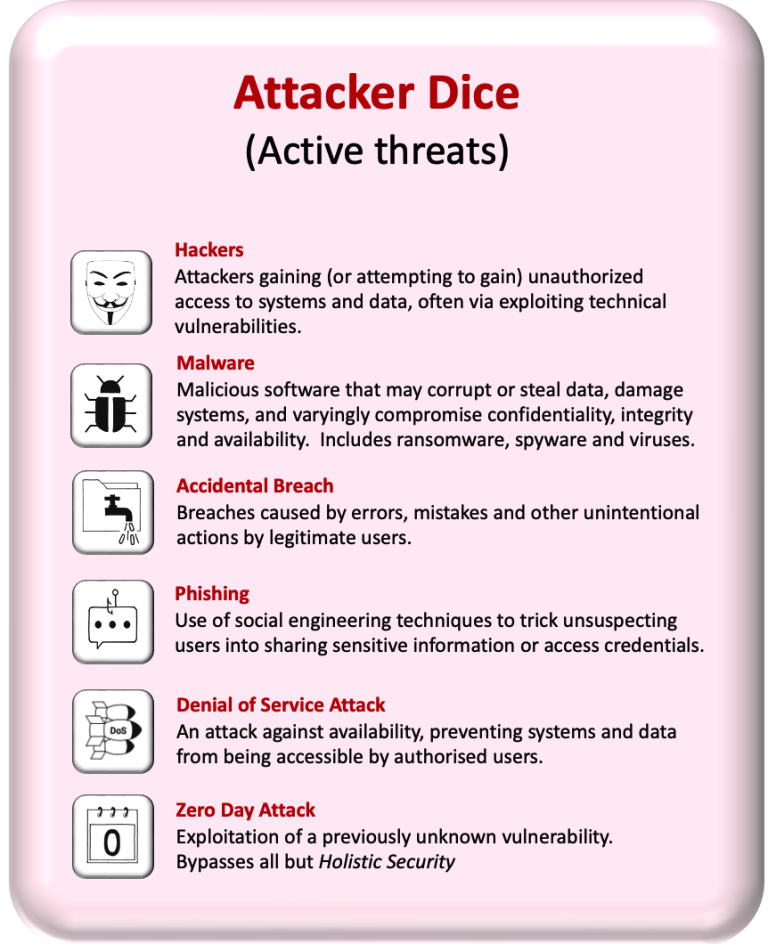


General rules
Each side (individual players or teams) gets a set of five dice – the red set for Attackers, the blue set for Defenders.
Each side has up to three throws but can choose to stop after one or two throws if preferred. The side throwing second is then limited to that number of throws.
There are three suggested games, each with different ways of using the dice and increasing complexity to play.
Game 1 – ‘Yahtzee’ rules
Each set of dice has a scale of importance (from lowest to highest):
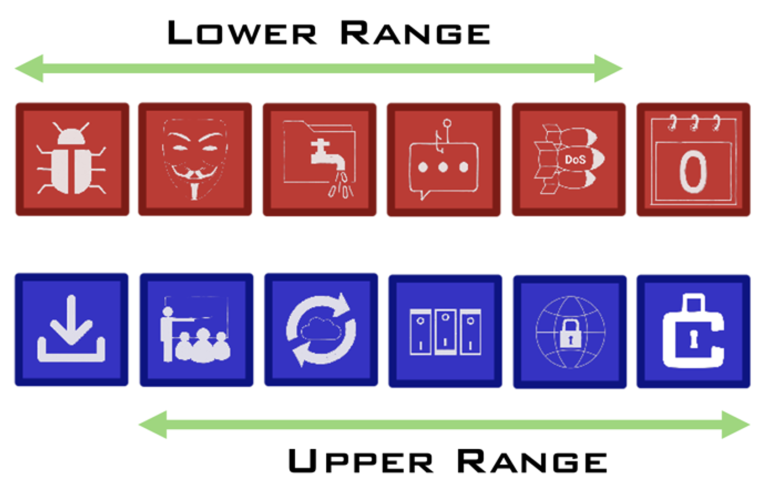
Valid dice combinations, in increasing order of value, are then:
- Two of a kind
- Two pairs
- Three of a kind
- Full range attack or defence (a full set of five different attacks or defences, with the upper range set beating the lower range)
- Combined attack or defence (three of one + two of another)
- Four of a kind
- Five of a kind
Game 2 – Combat mode
Either side may start the game, and play is then determined by the winner of prior rounds.
Responding players need to combat what the opening side has thrown, e.g.:
- if a Defender has opened play by throwing 4 Staff Awareness, the Attacker needs to target this via Phishing or Accidental Breaches (or via Zero Day Attacks which are valid attacks against all defences)
- if an Attacker has thrown 3 Phishing, then the Defender can counter with 3+ Staff Awareness or Internet Security (or via Holistic Cyber Security, which is a valid defence against all attacks)
To win a round players need to throw more defence dice than the corresponding attack (or vice versa) – e.g. if 2 Malware dice are thrown then defenders need 3+ of other relevant dice to defend (e.g. 3 Backup, 3 Configuration or 3 Internet Security).
If a matching number of attack/defence dice are thrown (e.g. 3 Malware and 3 Backup), then the round is a draw (no point scored).
Zero Day Attacks can only be defended by throwing:
- a corresponding number of Holistic Cyber Security dice
- a full range of other controls (Backup, Configuration, Updates, Internet Security, and Staff Awareness)
Holistic Cyber Security can be attacked by throwing:
- a corresponding number of Zero Day Attack dice
- a full range of other attacks (Malware, Hackers, Phishing, Accidental Breach, and DoS)
Turn taking
- If the Attacker throws first, they are potentially catching the victim unawares, and the Defenders are applying security in a responsive manner.
- If the Defender throws first, it’s like they’re deciding what to invest in and finding out if they chose correctly. For the attacker it’s like they’ve done reconnaissance and know what to attack.
- The winner of a round starts the next round – so a successful attack has the chance to escalate, and successful defence has a chance to maintain more effective protection.
Game 3 – Attack Matcher
- The attacker always throws first, and up to 3 times.
- The defender can then throw up to the same number of throws to obtain a set of dice that counter the attack.
- An attack is countered if, for each attacking die, there is a corresponding defending die that beats it (see below).
- Each defending die can only be used to counter one attacking die.
- If the attack is countered, the defender wins; and vice-versa!
Each attack die can be combatted by defence dice as follows:
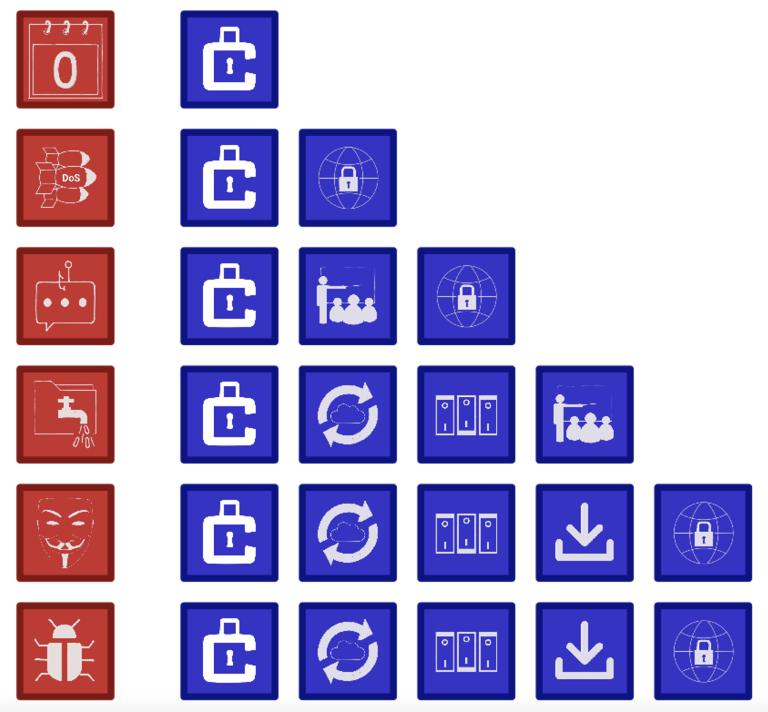
Cyber Defence Dice game concept and design
© Steven Furnell, Lucija Šmid, James Todd and Xavier Carpent, 2025.
© Copyright. All rights reserved.
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.
